Bitcoin Layer 2 Showdown: The Role of Security in Determining the Top L2
Explore the security mechanisms powering Bitcoin's top layer 2 solutions vying to become its dominant execution layer. From Lightning Network to Merlin Chain, discover how each L2 upholds Bitcoin's foundational values of security and decentralization in their quest for the crown.

To date, Bitcoin remains the most secure and decentralized blockchain, that is a fact! But this hard truth comes at the cost of scalability and as we have mentioned on many occasions, this limitation has kept it out on many DeFi activities. With its market cap of $1.5 trillion and on track to surpass gold, any Bitcoin L2 that enables Bitcoins involvement in these new activities could eventually be crowned as its dominant execution layer.
The only question is - which L2 will it be? Given that everyone backing Bitcoin prioritizes security above all else, any L2 aiming for this role must offer strong security features.
Join us in this article, as we take a look at the security mechanisms of prominent Bitcoin layer 2 solutions, and assess how each positions itself as a contender in this quest.
A Look at the Bitcoin Layer 2 Landscape
In general, a layer 2 solution refers to a protocol built on top of an underlying blockchain base layer with the aim to scale it. As we mentioned a lot in our previous articles.

However, when it comes to Bitcoin, it is important to acknowledge that L2s have broader goals than on other base layers. For instance, while the primary motivation for Ethereum L2s is to enhance scalability, on Bitcoin they serve the dual purpose of improving scalability and more importantly functionality.
To understand this distinction, consider this: Currently, Ethereum mainnet facilitates the majority of valuable ETH activity, and continues to dominate metrics and total value locked (TVL) as well as stablecoin issuance. Its layer two's are all much smaller by comparison.
However, a look at similar metrics for Bitcoin, suggests the opposite. For example, DeFi activity on Bitcoin is conversely distributed across L2 solutions.

But as we began by saying, the reason Bitcoin layer one has lagged behind is because it chooses to prioritize security above all else. Again, the Bitcoin base layer had never been breached.
Therefore, if any L2 is to become the heir to Bitcoins vast liquidity, it must first win over its community and the only way to achieve that, is to uphold the foundational security values.
With that in mind, let's now look at how various prominent Bitcoin L2s are approaching the issue…
Security Mechanisms of Various Bitcoin Layer 2 Solutions
When it comes to Bitcoin, security is analyzed through several key pillars, including decentralization, cryptography, consensus mechanisms, and immutability.

Because there are many moving parts, we will try to examine how various Bitcoin L2s achieve their security framework...👇
1) Bitfinity
First and foremost is our very own Bitfinity net, which is the EVM-compatible Bitcoin sidechain which brings the Ethereum development and experience to Bitcoin. For maintaining a bridge between these two biggest chains, Bitfinity uses a threshold cryptographic scheme called Chain-Key Cryptography coming from Chain Fusion technology that was introduced by the Internet Computer.
Chain-Key Cryptography
What is striking of this Chain-Key Cryptography is that is a security mechanism that allows independently owned, interconnected nodes that form a blockchain or subnet to collectively manage the cryptographic keys.
Central to this technology are canisters, which are similar to smart contracts on most blockchains. They store code, data, and state, with copies stored across the interconnected nodes.
For secure cross-chain communication, Bitfinity has incorporated a threshold Elliptic Curve Digital Signing Algorithm (tECDSA) signature scheme within these canisters across 40 nodes.
This means no single node of these 40 has full access to the threshold key and needs to approve a transaction more than one-third of these nodes to generate a threshold signature using their respective key shares.
With the keys that are regenerated every 11 minutes in a process known as 'moon-math'. For more technicals please check out the video below.👇
2) Liquid Network
Liquid Network also serves as a Bitcoin sidechain and has a two-way peg facility to allow Bitcoin holders to port their BTC where bridged to the Liquid Network is represented as L-BTC (liquid BTC).

Instead of using a proof-of-work consensus mechanism, Liquid Network uses an approach to consensus called ‘Strong Federations’ to serve as the creators of new blocks and secure the network.
Strong Federations
These 'strong' members, who operate the network, are composed of large exchanges, financial institutions, and Bitcoin-focused companies are geographically distributed worldwide. Among these members are 15 functionary operators who serve two roles on the network – as block signers to operate the Liquid sidechain, and as watchmen to secure Bitcoins held by the Network.
For security, the federated model requires blocks to be signed by at least two-thirds of the 15 functionaries.
Confidential Transactions
This is another key security mechanism where, unlike in Bitcoin, Liquid transactions hide asset type and amount from the public ledger. Not even the Liquid Federation members and functionaries can see this information. Only the sender, receiver, and those they choose to reveal it to can see these details. This is done through a process known as 'blinding'.

Although the amounts and assets are confidential by default, the Liquid network replaces them with cryptographic commitments. These commitments allow validators to add up the inputs and outputs to check that the results are equal, for assurance that no inflation or destruction of coins has occurred.
3) Stacks
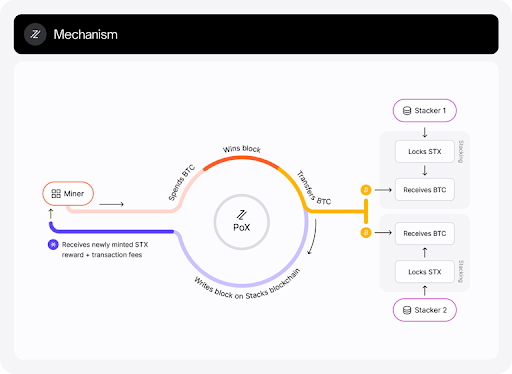
Stacks is also a Bitcoin sidechain, but unlike Rootstock, which depends on Bitcoin's PoW consensus mechanism for security, it runs its own consensus mechanism known as Proof of Transfer (PoX).

Proof of Transfer
Proof of Transfer is similar in spirit to Bitcoin's Proof of Work consensus. Like Bitcoin PoW miners spend electricity and are rewarded in BTC, Stacks PoX miners spend (already mined) BTC and are rewarded in STX (Stack's native token).
In addition, PoX is permissionless, which means anyone can be a Stacks miner as long as they spend BTC. Also, any STX holder can lock their STX in a process called 'stacking' to participate in PoX consensus.
Bitcoin Finality
To inherit this security mechanism, Stacks has 100% Bitcoin finality, meaning it is as difficult to reverse a Stacks transaction as it is to reverse a Bitcoin transaction. This was made possible through the 2024 Nakamoto release.
Bitcoin finality refers to the point at which a Bitcoin transaction or block of transactions is considered permanently confirmed and cannot be undone or changed, typically after six confirmations (60 minutes).
Decentralized sBTC Bridging
The Nakamoto upgrade also facilitated sBTC, a 1:1 Bitcoin-backed asset, that enabled users to put their BTC to work in DeFi, dApps, and other applications. But unlike Rootstock and Liquid Network, where the pegged assets are managed by a federation, sBTC is decentralized.
It is maintained by a permissionless, open-membership group of dynamically changing Stackers of the PoX consensus protocol who can start or stop contributing to peg maintenance as they please. For safe sBTC withdrawals, the system requires that at least 70% of the Stackers approve it.
And as we saw earlier, the incentive design of BTC rewards and the stacking of STX as collateral gives them clear economic motivation to properly maintain the peg. In addition, sBTC also leverages Stacks' 100% Bitcoin finality.
4) BitVM
BitVM is a project that enables Bitcoin to support Turing-complete smart contracts and to ensure it maintains Bitcoin's foundational security values, BitVM makes use of optimistic computation where the computing party is assumed to be honest until proven otherwise by challengers through fraud proofs and a challenge-response protocol.
The Prover-Verifier Model
The fraud proofs and the challenge-response protocol is based on two parties; the prover who executes computations off-chain and commits the results on-chain and a verifier who monitors these commitments and can challenge incorrect results. To enforce honesty, both parties deposit funds into an address linked to the 2021 Taproot upgrade.
To challenge a computation, a challenger must simply execute its respective sub-programs on-chain in a Bitcoin transaction, showing a mismatch between the computation and the prover's claim. Through the latest upgrade to BitVM2 anyone can be a challenger and requires only 3 on-chain transactions to initiate a challenge. If found guilty some of the prover's deposits are slashed to cover on-chain costs.
5) Bitlayer
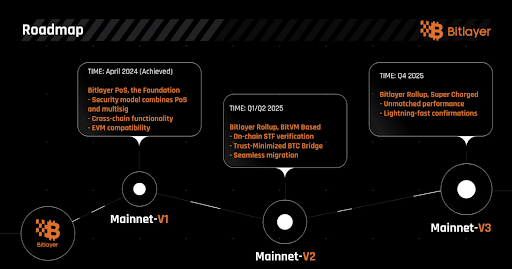
Built on the BitVM, Bitlayer functions as an EVM-compatible, smart contract-capable solution for Bitcoin. As a scaling solution, Bitlayer is positioned to evolve through different stages, with several already achieved and others underway.
The first stage is its foundational stage that mainnet went live in April, 2024. In this stage, it adopts a security model that combines Proof of Stake (PoS) with multi-signature technology based on the MuSig2 implemented as BIP-327.
Under MuSig2 the required number of signatures to approve a transaction depends on the specific configuration chosen during the setup of the multi-signature arrangement.

For instance, Satoshi, Vitalik, and Hal Finney can choose to set up a 3-of-3 multi-signature wallet; this means that the three of them must sign a transaction for it to be valid. Also, they can choose a 2-of-3 multi-signature arrangement where only two of them are required to validate a transaction.
This fist stage was achieved through collaboration with multiple custody platforms, such as Coinbase Ventures, which are responsible for proposing blocks and maintaining the Bitlayer blockchain.
The second stage, expected in Q1/Q2 2025, will transition Bitlayer into a native Bitcoin rollup. This will allow it to achieve Bitcoin-equivalent security by verifying state transitions directly on Bitcoin L1.
6) Merlin Chain
Merlin Chain serves as a Bitcoin L2 built on the rollup design and with it, it has a security model based on three key technologies: zero-knowledge, decentralized oracle networks, and an on-chain BTC fraud-proof model.
Zero-knowledge Technology
Merlin Chain scales Bitcoin through zkEVM, an EVM-compatible scaling solution that uses zero-knowledge proofs to prove the validity of state changes. These proofs are generated by zkProvers who then send them to the sequencer nodes for further verification and recording to the Bitcoin base layer.
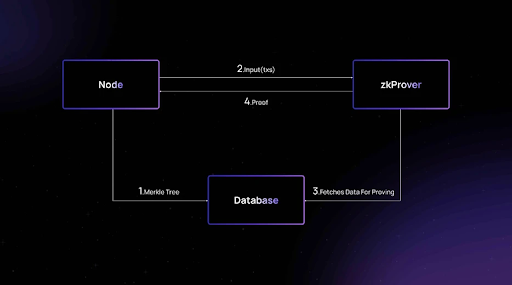
Decentralized Oracle Network and the BTC Fraud-Proof Mode
To record state changes, sequencer nodes depend on an oracle network. This network consists of nodes whose job is to confirm the handling of transaction data received from the sequencer nodes. Therefore, they must remain honest.
To ensure they do, Merlin Chain requires all oracle network nodes to stake BTC before participating. This allows users to challenge the validity of ZK-proofs and batched data. If a challenge succeeds, the oracle network node that confirmed the transactions loses a fraction of their staked BTC. In addition, Merlin Chain employs multi-signature and cold storage technologies to secure the staked assets.
𝗠𝗲𝗿𝗹𝗶𝗻 𝗗𝗲𝘃𝗲𝗹𝗼𝗽𝗲𝗿 𝗨𝗽𝗱𝗮𝘁𝗲: 𝟯𝟭𝘀𝘁 𝗠𝗮𝘆, 𝟮𝟬𝟮𝟰
— Merlin Chain (@MerlinLayer2) May 31, 2024
𝗠𝗲𝗿𝗹𝗶𝗻 𝗣𝗼𝗦 𝗨𝗽𝗴𝗿𝗮𝗱𝗲 𝘄𝗶𝘁𝗵 𝗠𝗣𝗖 𝗦𝗼𝗹𝘂𝘁𝗶𝗼𝗻
📍 𝗞𝗲𝘆 𝗨𝗽𝗱𝗮𝘁𝗲𝘀
🔸 Prevent single points of failure via MPC solutions provided by Cobo, Fireblocks, Antalpha and New Huo Tech.
🔸… pic.twitter.com/12b0ZGg02o
This way each party signs the transaction together without exposing each other's private key shards. However, the exact number of members in the MPC required to sign a transaction is not specified.
7) Rootstock
Rootstock (RSK) operates as a Bitcoin sidechain, which means it can run its own consensus mechanism but still maintain a level of communication with the main network. To scale Bitcoin, it uses a two-way peg system that allows the transfer of assets between the two networks. For the purpose of security in these activities, RSK uses the following mechanisms.

PowPeg
The two-way peg between Rootstock and Bitcoin functions by locking BTC in the Bitcoin blockchain and unlocking the same amount in Rootstock in the form of RBTC (peg-in).
When RBTC needs to be converted back into BTC, it gets locked again in Rootstock and the same amount of BTC is unlocked in Bitcoin (peg-out).
For fully trust-minimized and third-party-free two-way pegs like these, the two networks must have Turing-complete smart contracts. But as we know, the Bitcoin base layer does not currently support these types of smart contracts. Therefore, to ensure security of locking and unlocking of these funds, Rootstock has implemented a semi-trusted third-party system they call PowPeg.
The system is made up of a federation that uses multi-signature wallets and hardware security modules called PowHSMs that operate an RSK node in Simplified Payment Verification (SPV) mode. In this mode signatures can only be authorized through cumulative Proof of Work (PoW), which as we know is Bitcoin's consensus mechanism and works on the longest chain rule.
Therefore, peg-in and peg-out transactions on RSK require a high number of block confirmations. Peg-ins require 100 Bitcoin blocks (approximately 2000 RSK blocks), and peg-outs require 4000 Rootstock blocks (approximately 200 Bitcoin blocks).
To achieve this, Rootstock depends on a technique known as merged mining.
Merged mining is a technique where the same mining hashrate that secures a primary blockchain is used to secure a secondary blockchain. For Rootstock, the primary blockchain is of course Bitcoin.
Final Thoughts
As is the nature of the market, the strength of any asset as 'money' depends on its functionality across many properties. Although Bitcoin with its immutable security has positioned itself as a perfect option for this, it lacks that base support for the many properties.
This is where L2s came to offer a helping hand each with an aim to be the best contender in this . But while doing so it is important that they remember that Bitcoin made a sacrifice to be the way it is but maintain security. Therefore, if any of them is to succeed in this quest, their fate hinges on upholding these foundational values.

Connect with Bitfinity Network
Bitfinity Wallet | Bitfinity Network | Twitter | Telegram | Discord | Github

*Important Disclaimer: The information provided on this website is for general informational purposes only and should not be considered financial or investment advice. While we strive for accuracy, Bitfinity makes no representations or warranties regarding the completeness, accuracy, or reliability of the content and is not responsible for any errors or omissions, or for any outcomes resulting from the use of this information. The content may include opinions and forward-looking statements that involve risks and uncertainties, and any reliance on this information is at your own risk.
External links are provided for convenience, and we recommend verifying information before taking any action. Bitfinity is not liable for any direct or indirect losses or damages arising from the use of this information.














Comments ()